NEWS - ALERTS:
General Security Information (including Phishing Scams):
-
Safe Email Practices
-
Safe Internet Browsing Practices
-
How to Avoid Phishing Scams
-
Link (lifewire.com - article - How to test a Suspicious Link):
Email SPAM and Phishing
How to "REPORT" SPAM or Phishing emails? Forward original email to: abuse@fsu.edu
Possible Affected Systems: Any University Account

FSU faculty, staff and students are receiving more and more sophisticated, targeted email phishing attempts. Most current phishing email look quite convincing until you look at the details of the message; who it came from, what are they asking for, details that are incorrect (wrong address, phone number, name, etc.), where they want to send you (links in the message to odd URLs), etc. We continue to see long emails detailing changes to your account which are false or even short message with spoofed sender information (name on the ‘From’ looks correct, but when you hover over the ‘From’ it shows an incorrect or odd email address).
Digitally signed files are a part of many FSU business processes, and are often passed around via automated emails. It is also a clever method used by criminals to hide malicious payloads. This method of phishing has become more common because the emails don't always look like they came from a human anyway, so those targeted are.
For example, here is a fake DocuSign email:
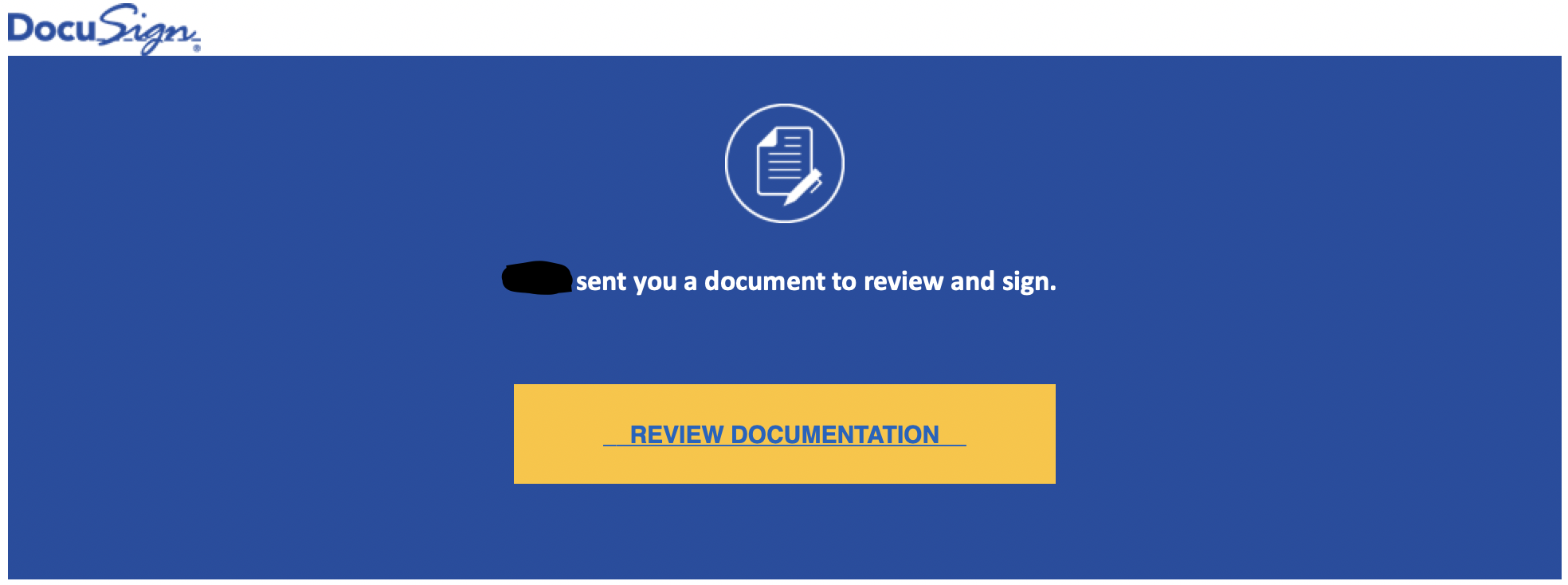
The malicious part of this email is following the link:

Reviewing information found in the email's FROM and TO makes this very suspicious - it was sent from a person I have no contact with, from a @my.fsu.edu (which is a student email) and the TO is completely missing:

Seeing an email, like this above, please feel free to contact us and have us review the message - if you feel it might be real.
Be alert and definitely be suspicious of emails requesting account information or requiring you to immediately pass privileged information back to the sender or through a link (URL).
Phishing emails are crafted to appear as though they have been sent from a legitimate organization or known individual. These emails often entice users to click on a link or open an attachment or URL link containing malicious code. After the code is run, your computer may become infected with malware. In some cases, the user may be directed to a site that is tailored to look like valid University login systems - make sure to review the URL in the browser.
A commitment to cyber hygiene and best practices is critical to protecting organizations and users from cyber threats, including malware.
In advice specific to any Phishing threat, users should:
- Be careful when clicking directly on links in emails, even if the sender appears to be known; attempt to verify web addresses independently (e.g., contact your organization's helpdesk or search the Internet for the main website of the organization or topic mentioned in the email).
- Exercise caution when opening email attachments. Be particularly wary of compressed or ZIP file attachments.
- Follow best practices for Server Message Block (SMB) and update to the latest version immediately. (See US-CERT’s SMBv1 Current Activity for more information.)
For general best practices on patching and phishing, users should:
- Ensure that your applications and operating system has been patched with the latest updates. Vulnerable applications and operating systems are the target of most attacks. (See Understanding Patches.)
- Be suspicious of unsolicited phone calls, visits, or email messages from individuals asking about employees or other internal information. If an unknown individual claims to be from a legitimate organization, try to verify his or her identity directly with the company.
- Avoid providing personal information or information about your organization, including its structure or networks, unless you are certain of a person's authority to have the information.
- Avoid revealing personal or financial information in email, and do not respond to email solicitations for this information. This includes following links sent in email.
- Be cautious about sending sensitive information over the Internet before checking a website's security. (See Protecting Your Privacy.)
- Pay attention to the URL of a website. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com vs. .net).
- If you are unsure whether an email request is legitimate, try to verify it by contacting the company directly. Do not use contact information provided on a website connected to the request; instead, check previous statements for contact information. Information about known phishing attacks is also available online from anti-phishing groups such as the APWG.
- Install and maintain anti-virus software, firewalls, and email filters to reduce some of this traffic. (See Understanding Firewalls, Understanding Anti-Virus Software, and Reducing Spam for additional information.)
If you believe that you have been a victim of a phishing attack or ransomware infection, immediately report the incident to our College IT Support Team (Request Support page) or to ITS' Service Center (https://help.fsu.edu/).
Top FAQs:
Access - Network File Shares/Folders
Adobe Creative Cloud (aka. CC)
Cisco AnyConnect (VPN)
FSUID
OneDrive for Business
- OneDrive for Business - Quick Start Guide
- Thank you Department of Mathematics!
- OneDrive - Save Disk Space with Files On-Demand
Qualtrics
- Select this link, then Download at the top left of the page for Set Date logic for Qualtrics. Java Script
- Select this link, then Download at the top left of the page for Guide for updating a survey. Java Script
Zoom for Instructors and Students
- How to Keep Uninvited Guests Out of Your Zoom Event
- Zoom Troubleshooting and FAQ for Instructors and Students
- Thank you Department of Mathematics!
- When saving a Zoom chat, where is it?
- Quick answer: Go to Documents folder, then Zoom folder, and then Folder with meeting name, date and time.
Email - Information:
Microsoft and FSU plan to require all email clients connecting to FSU's email servers to use a new authentication and authorization method by October 2022, called OAuth 2.0. A number of email clients have already been connected to FSU's email servers using OAuth 2.0. On Monday March 28th, FSU sent an email to users who have been identified as potentially having an older, non-OAuth 2.0 client connecting to the University email servers. The email would look something like the following:

Below is some general information and FAQs which we have been fielding for the past day, in hopes to pass along some additional information to you.
NOTE: You may often see OAuth 2.0 called Modern Authentication method below.
General Information and FAQ - OAuth 2.0
- Why is the University and Microsoft requiring this new Modern Authentication method (OAuth 2.0)?
- Basic Authentication makes it easier for attackers armed with today’s tools and methods to capture users’ credentials and increases the chance of credential re-use. The move to Modern Authentication will help protect data in the Microsoft 365 (also known as O365) cloud.
- I didn't receive an email as shown above, do I need to do anything?
- No, if you did not receive an email as shown above, you do not need to do anything.
- What will happen to my email on FSU's servers if I do not update my client(s)?
- Nothing will happen to your email on the servers. The change only affects the connection of an email client to your email stored on the servers. Also, this interruption will no occur until ITS or Microsoft requires the OAuth 2.0 Modern Authentication method.
- What does it mean to delete an account from within your email application (Mac Mail [macOS, iOS, and iPadOS], Thunderbird, and MS Outlook)?
- Deleting the account information means you will delete the settings which connect your email application to the email server. No emails would be deleted, just the connection settings.
Apple Mail FAQ
- What versions of Apple Mail are compatible with the new Modern Authentication method?
- macOS 10.14 (or later)
- iOS 11 (or later)
- iPadOS 13.1 (or later)
- NOTE: the most recent versions of Mac Mail clients have been tested. It will work with the OAuth 2.0 Modern Authentication method, but is not supported by FSU ITS.
- I received the email shown above and I am running a OS that is compatible above, what do I need to do?
- We recommend that you contact us and schedule a time to have a technician work with you on updating your email settings.
- If you want to update your settings, the process requires that you delete your current account setup and then perform a new setup of your FSU email account.
- How do I setup FSU email in Mac Mail?
- Please follow these instructions (NOTE: stop before you reach the section 'Outlook for Mac'): https://fsu.force.com/s/article/How-do-I-set-up-my-FSU-email-on-Mac
Mozilla Thunderbird FAQ
- What versions of Mozilla Thunderbird are compatible with the new Modern Authentication method?
- Thunderbird version 78 (or later)
- NOTE: the most recent version of the Thunderbird email client has been tested. It will work with the OAuth 2.0 Modern Authentication method, but is not supported by FSU ITS.
- How do I setup FSU email in Mozilla Thunderbird?
- Please follow these instructions: https://fsu.sharepoint.com/:w:/s/coas/casits/EY-F45D8K1xNhRyRfUE9bkIBg9Na1Sk6EXCrteRc7e__VA?e=1MJPXp
FSU Webmail FAQ
- What do I need to know about FSU's webmail and the new Modern Authentication method?
- Webmail (https://outlook.com/fsu.edu) is not affected by this change. The Modern Authentication method is integrated into the website, you don't need to do anything.
MS Outlook FAQ
- What versions of MS Office (which includes Outlook) are compatible with the new Modern Authentication method?
- Office 2016, Mac Office 2016, Office 365, Office 365 ProPlus 2019 (or later); are all compatible with the new Modern Authentication method.
- I received the email shown above but I have only ever used a version of Office listed on the compatible list. What do I need to do?
- You should not need to do anything. We have received a number of reports of users receiving this email but they are using the latest or a compatible version of Office, but we have found that nothing needs to be changed.
- We recommend checking to see if you are connecting to your email account from a mobile device and its mobile Operating System's default email client. This could be a where an Older Authentication method has/is being used.
- If you do receive a followup, please reach out and contact us.
- I am using an older version of MS Office which is not on the compatible list. What do I need to do?
- Please contact us as soon as possible and we will work to schedule a time to update your version of MS Office.
- NOTE: it is possible that your Windows OS or macOS may need to be updated. We will work with you to schedule a time to perform a full OS and system update.
- How do I setup MS Outlook for a mobile device?
- Please follow these instructions: https://fsu.force.com/s/article/How-do-I-set-up-my-employee-email-on-the-Outlook-mobile-app-1600352497229
- How do I set up my FSU email in Outlook 2016/2019?
- Please follow these instructions: https://fsu.force.com/s/article/How-do-I-set-up-my-FSU-email-in-Outlook-2016-2019-1600352296670
- How do I setup FSU email in Outlook for Mac?
- Please follow these instructions (NOTE: scroll down to the section 'Outlook for Mac'): https://fsu.force.com/s/article/How-do-I-set-up-my-FSU-email-on-Mac

